
Taiwan Bounty: PRC Cross-Agency Operations Target Taiwanese Military Personnel
Taiwan Bounty: PRC Cross-Agency Operations Target Taiwanese Military Personnel
Executive Summary:
- For the first time, public security authorities in the People’s Republic of China (PRC) are targeting Taiwanese military personnel and so-called “Taiwan independence” (台独) forces through a law enforcement framework. Akin to techniques previously used in Hong Kong, the Guangzhou Public Security Bureau recently issued a “wanted” notice offering a reward for information leading to the apprehension of 20 retired and active personnel in Taiwan’s Information, Communication, and Electronic Force Command (ICEFCOM).
- The operation appears to involve close coordination between the Public Security Bureau and state media outlets. Within minutes of the announcement, the photos and ID numbers of the 20 Taiwanese personnel were plastered across the Chinese Internet, as was a detailed report purporting to show how they had launched a cyberattack against PRC institutions.
- Part of a growing trend of cyber and psychological warfare tactics, this latest operation sought to reframe the issue by portraying the PRC as a victim and Taipei as an aggressor, while also aiming to deter any future pro-independence activities by threatening punishment.
Over the past two years, Hong Kong authorities have placed bounties on 19 prominent pro-democracy activists of Hong Kong Dollar (HKD) 1 million ($127,000). The People’s Republic of China (PRC) now appears to be extending similar tactics to its broader hybrid warfare playbook, this time targeting Taiwan’s military personnel. In early June, the Guangzhou Public Security Bureau (PSB) issued a “wanted” notice offering a renminbi (RMB) 10,000 ($1,400) reward for information leading to the apprehension of 20 retired and active personnel in the Information, Communication, and Electronic Force Command (ICEFCOM; 國防部資通電軍指揮部) of Taiwan’s Ministry of National Defense (MND).
This marks the first known instance of PRC public security authorities targeting Taiwanese military personnel and so-called “Taiwan independence” (台独) forces through a law enforcement framework. The level of cross-agency coordination involved in the operation far exceeds the norm for local PSB branches. It engaged state and state-affiliated entities across multiple domains, employing mutually reinforcing tactics, techniques, and procedures (TTPs). Its goal was to erode morale and exert psychological pressure on Taiwan’s military while discrediting its reputation in the public sphere, ultimately deterring pro-independence sentiment and obstructing perceived challenges to Beijing’s broader reunification agenda.
Coordinated Cross-Agency Operation
On the morning of June 5, the Tianhe Branch of the Guangzhou PSB issued a “wanted bounty notice” (悬赏通告) targeting 20 personnel from Taiwan ICEFCOM. The announcement was a response to an accusation that a “hacker organization” (黑客组织) linked to the Democratic Progressive Party (DPP) government had launched a cyberattack against a PRC tech company (Weibo/Guangzhou PSB Tianhe Branch, June 5).
Within two minutes of Tianhe PSB’s Weibo post, PRC state media Xinhua amplified the bounty notice, reposting the same photo and personal information of the 20 listed “suspects” (嫌疑人) (Xinhua, June 5). It also cited a joint report released on the same day by the PRC National Computer Virus Emergency Response Center (CVERC, 国家计算机病毒应急处理中心) and 360 Digital Security Group (360数字安全集团) as “detailed evidence” of ICEFCOM’s alleged crime. The 43-page joint technical report supports PSB’s claim that ICEFCOM was involved in cyberattacks against PRC institutions. It alleges that these actions form part of a broader effort to support long-term U.S. government and military strategies—including information, public opinion, and cognitive warfare—intended to sow social discord, threaten PRC national security, and obstruct Beijing’s “reunification” agenda. Beyond outlining ICEFCOM’s mission, structure, and operations, it also discloses personal details for six additional senior officers—none of whom are listed in the bounty notice (CVERC, June 5).
Over the next three hours, all major PRC state media—including Xinhua, China Central Television (CCTV), People’s Daily, China News Service (CNS), China Global Television Network (CGTN), Global Times, and China Daily—amplified the allegation and bounty notice using near-identical headlines and content (CCTV; People’s Daily; CNS; CGTN; Global Times; China Daily; June 5).
Figure 1: Relationship Between PRC State and State-affiliated Entities Targeting Taiwanese Military Personnel
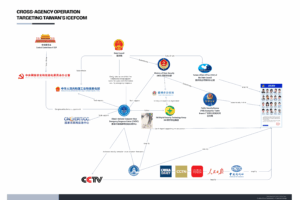
(Source: Author)
By mid-afternoon, the Taiwan Affairs Office (TAO) had shared the news across its website and social media accounts, and domestic media outlets and key opinion leaders (KOLs) provided further dissemination over the following days (Taiwan Affairs Office, June 5). Notably, some posts were published in English and traditional Chinese, and shared on platforms such as Facebook and YouTube that are popular among Taiwanese users, suggesting a targeted effort to influence both international and Taiwanese public opinion (Facebook/Taiwan.cn; YouTube/Taiwan.cn, June 6).
The involvement of national media and state-level agencies in actively amplifying the accusation contrasted with minimal coverage from either the Tianhe PSB itself—restricted to three Weibo posts on May 20, May 27, and June 5—or the websites and official social media accounts of the Guangzhou Tianhe District Government and Guangzhou PSB, which both remained silent (Weibo/Guangzhou PSB Tianhe Branch, accessed June 5). The first two posts were “Police Notices” (警情通报) stating that the PSB initially assessed the cyberattack against the Chinese tech company to have been launched by foreign entities, and later attributed the attack to the DPP administration (Weibo/Guangzhou PSB Tianhe Branch, May 20, May 27). This suggests the operation was a part of a broader, coordinated effort beyond the scope of a single municipal-level PSB branch.
Hybrid Warfare Targets Taiwan’s Military Personnel
The “Taiwan bounty” operation marks the PRC public security authorities’ first attempt to target Taiwanese military personnel and “independence forces” through domestic legal frameworks and law enforcement measures. The coordinated, cross-agency nature of the operation underscores its strategic importance. It may also indicate that ICEFCOM’s work has proven effective in countering PRC information warfare efforts to date.
While the bounty approach might be new, it is not the PRC’s first attempt to defame Taiwan’s ICEFCOM. Earlier efforts were led by a different state agency, the Ministry of State Security (MSS). On September 22, 2024, the MSS accused a hacker group named “Anonymous 64” (匿名者64), allegedly managed by ICEFCOM, of launching frequent cyberattacks on the PRC, Hong Kong, and Macau, and of spreading disinformation about Beijing’s political system and policies (WeChat/Ministry of State Security, September 22, 2024). The MSS post that made the accusation included the doxxing of three ICEFCOM personnel. On March 17, the MSS released another post exposing four more ICEFCOM officers. This post also provided multiple channels, including a hotline, an online platform, and an in-app WeChat function, for submitting reports about these individuals (WeChat/Ministry of State Security, March 17).
The involvement of the MPS and PSBs in the latest operation signals a more integrated and sophisticated approach to targeting Taiwanese military personnel—one that combines psychological warfare, lawfare, and social media influence operations. Under this model, the MPS and local PSBs first initiate allegations, issue arrest warrants, and announce bounty notices through the PRC’s legal system. Multiple laws have been invoked to justify these actions, including the Criminal Law (刑法), Cybersecurity Law (网络安全法), Counter-Espionage Law (反间谍法), and Anti-Secession Law (反分裂国家法). In addition, the 2024 judiciary guidelines titled “Opinions on Punishing the Crimes of Secession and Incitement to Secession by ‘Taiwan Independence’ Diehards According to the Law” (关于依法惩治“台独”顽固分子分裂国家、煽动分裂国家犯罪的意见) have been repeatedly cited to legitimize these increasingly assertive measures. (Ta Kung Pao, June 6)
The MPS and PSBs then coordinate with state agencies and state-affiliated cybersecurity firms, which bolster the accusation by providing supporting evidence of the alleged crime. In this case, the CVERC and 360 Digital Security Group-authored technical report served this purpose.
A third step further weaponizes these accusations by building a wider influence operation. One part of this step involves PRC state and state-affiliated media broadcasting a unified narrative aimed at demonstrating the PRC’s superiority. In this case, the narrative portrayed the PRC as possessing superior cyber capabilities, Taiwan’s cyber defenses as ineffective, and “reunification” as inevitable and unchallengeable. Another part is the use of relevant government agencies to make assertive claims—in this case, using the TAO to frame the operation as part of the broader campaign to punish “separatists” (分裂势力).
These influence operations serve dual purposes. First, they seek to reframe the issue to reflect Beijing’s preferences. This entails portraying the PRC as a victim and Taipei as an aggressor provoking cross-strait conflict by engaging in criminal activity—a narrative ploy to justify Beijing’s assertive actions and extra-territorial law enforcement. The second purpose is to deter actions that go against Beijing’s preferences. By clearly articulating the (largely symbolic) arrest warrants and cash bounties, the PRC likely aims to dissuade pro-independence activities by threatening punishment for individuals involved in countering the PRC’s cyber, information, and cognitive warfare efforts against Taiwan. The exposure of detailed information about ICEFCOM and doxxing its personnel—by releasing photos and ID numbers—constitutes a further psychological deterrent. Even the title of the CVERC report, which includes the idiom “蚍蜉撼树”—literally, “an ant trying to shake a tree”—is intended to underline the futility of resistance. In this way, the operation also aims to legitimize extraterritorial law enforcement and even encourage surveillance and harassment of wanted individuals.
Each element of this hybrid warfare approach reinforces the others, aiming to erode morale, apply psychological pressure on Taiwan’s military, and damage its public credibility. Taken together, these measures aim to deter pro-independence efforts and any actions perceived as hindering Beijing’s broader reunification agenda.
Trend of Intensifying Psychological Operations
Recent developments suggest a growing trend of intensified psychological operations targeting Taiwan military personnel and “independence separatists.” In addition to accusations leveled against ICEFCOM by the MSS and MPS/PSB, the TAO has also escalated its efforts. On March 26, the TAO launched a dedicated webpage on its official website titled “Reporting column for the malicious acts of ‘Taiwan independence’ separatists and accomplices persecuting fellow Taiwanese” (‘台独’打手、帮凶迫害台湾同胞恶劣行径举报专栏). While presented as a new initiative, previous data indicate the platform was originally introduced on August 2, 2024 (TAO, August 2, 2024). Shortly after this apparent relaunch, the TAO claimed that it had garnered significant public attention—reporting 323 emails on the evening of its “launch day” and nearly 6,000 emails within two months (Taiwan Affairs Office, March 26, May 14).
Additional lawfare and psychological operations occurred during the same three months, including an announcement by TAO of sanctions against a company owned by the father of Puma Shen (沈伯洋), a member of Taiwan’s Legislative Yuan (TAO, June 5). [1] TAO claimed the measure as a punishment for pro-independence individuals and a warning that affiliated entities would be barred from profiting in the PRC.
Additional evidence indicates that these actions are interconnected. On June 5, PRC state media Xinhua first published an article on the “Taiwan bounty” at 08:01 am (China Standard Time). Within 30 minutes, it also reported on the TAO’s sanction, with the TAO using the content to publish it as “Important News” (要闻) on its website shortly thereafter (Xinhua; TAO; June 5). The well-orchestrated timing of the operations provides abundant materials for subsequent influence operations aiming to frame Taiwan as a provocateur while falsifying an image of Beijing’s targeted and all-around attack on “separatism.” For instance, on June 8, Xiake Island (侠客岛)—a WeChat account managed by People’s Daily—published an article titled “Taiwan’s so-called ‘mystery unit’ is exceptionally weak” (台湾的‘神秘部队’弱爆了). The piece synthesized content from previous MSS disclosures, the PSB’s bounty notice, and the TAO’s sanctions against the company owned by Puma Shen’s father to project an image of a decisive and effective crackdown on the pro-independence movement. It also warned that “more severe actions will follow” (后续将推出更多的狠招) (WeChat/Xiake Island, June 8).
An examination of the timeline between March and June suggests that these PRC operations often coincide with countermeasures Taipei takes against PRC hybrid threats, as well as politically significant events with strategic implications for Taiwan (See Figure 3 below). These include President Lai Ching-te’s (賴清德) designation of the PRC as a “foreign hostile force” (境外敵對勢力) and the rollout of 17 national security measures, the first anniversary of Lai’s inauguration, former Taiwan President Tsai Ing-wen’s (蔡英文) trip to Europe, and high-profile mainland events like the Cross-Strait Chinese Culture Summit and the 17th Strait Forum (CNA, March 13; MOFA, May 20; Xinhua, June 14). This integrated approach likely attempts to isolate the pro-independence camp and deter both its supporters and the general public from taking actions that might challenge Beijing’s asserted sovereignty claim over the island.
Figure 2: TAO’s Introduction of the Reporting Mechanism on August 2, 2024 (Top); TAO’s Repackaging the old Mechanism and Presenting it as a new ‘Reporting Column’ on March 26 (Bottom).


(Source: Screenshots from the TAO website)
Figure 3: Timeline of PRC Cross-Agency Operations and Taiwan Activities (March–June 2025)

(Source: Author)
Conclusion
The reality behind the PRC’s supposed exposé of ICEFCOM-linked cyberattacks on mainland institutions contrasts with its official narrative. The telling detail is the nature of the accusation referenced in the Tianhe PSB’s original announcement, which revealed minimal information about the alleged attack or the affected organization. In fact, the accusation appears to be fabricated. The attempt to dox military personnel was also based on inaccurate information, according to Taiwan’s Defense Minister. In a statement, the minister said that the defamation campaign was largely assembled using outdated open-source information, including data from old Facebook profiles. As a result, two-thirds of the listed individuals had already retired from military service (SETN, June 11).
However, it is noteworthy that at least some of the objectives behind the operation appear to have been achieved. These likely include eroding Taiwan citizens’ confidence in their government and damaging morale (though psychological effects are difficult to assess accurately)—the influence operation has received widespread coverage in Taiwan, leading to increased scrutiny of the government (SETN, June 11). The integrated nature of Beijing’s hybrid warfare—characterized by cross-agency coordination and intensifying psychological operations—as well as the specific targeting of Taiwanese military personnel and pro-independence individuals indicates that the PRC’s deterrence strategies are increasingly focused on individuals and organizations it sees as hostile.
Beijing’s hybrid warfare playbook is designed for replication far beyond its immediate periphery. The bounty cases in Hong Kong and Taiwan are likely merely the beginning of increasingly expansive and assertive behavior overseas (China Brief, July 17). Operations against those who do not toe the line on issues the PRC sees as critical to its national security are set to ramp up in the months and years ahead.
Notes
[1] Puma Shen has previously written for China Brief (China Brief, February 16, 2024).


